-
Oh boy, it looks like Vodaphone is actively attaching unique user IDs based at the SIM-card level to subscriber network requests. trustpid.com/
-
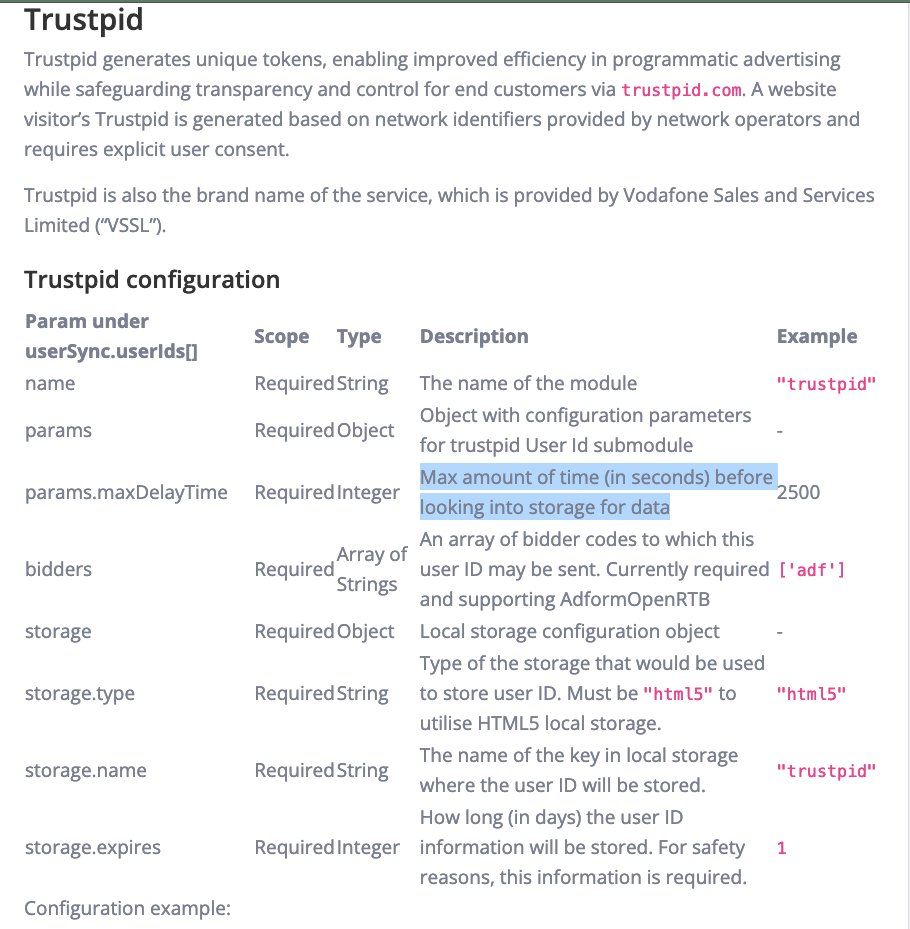
Are people transacting on this? Dunno, but uhhh it is in Prebid now - docs.prebid.org/dev-docs/modules/userId.html#trustpid
-
johnnyryan Curious if you've seen this already and if you think this works under GDPR with the way they are describing the opt out process?
-
Ad Tech going full Team America these days. If you want to use the internet you gotta pay your buck o'five worth of user data. youtu.be/tzW2ybYFboQ
-
And there's a *delay*? I'm assuming a mechanism for putting it in storage is provided because most sites are not prepared to take action off of HTTP headers so there is a methodology that handles it for them...
-
Looks like Vodaphone is indeed putting it in local storage somehow? github.com/prebid/Prebid.js/blob/997961fe1c10ac8e647b1ba019a1b189983daf9d/modules/trustpidSystem.js#L82
-
Even more interesting... it isn't just Vodaphone's domain listed as a participant! Apparently other domains that service Trustpid (somehow) include German T-Mobile and massive French telecom Orange, (which is >20% owned by the French state) github.com/prebid/Prebid.js/blob/997961fe1c10ac8e647b1ba019a1b189983daf9d/modules/trustpidSystem.js#L46
-
In case you were wondering... it *is* supported by Index github.com/prebid/Prebid.js/blob/3f99fa7b0b253c4730faf145d7f542c181a7b158/modules/ixBidAdapter.js#L78
-
-
Curious about browsers & extensions interested in preserving their privacy promises in this equation. Do they start blocklisting the localStorage keys? How do you deal with the telecom provider doing this?
-
Worth noting that Trustpid's per-site compliance mechanism appears to be working with CMPs which means that you could deny consent for Trustpid to be used on the page but the nature of TCF means that the ID will still be sent but with a string saying 'hey, don't use this'.
-
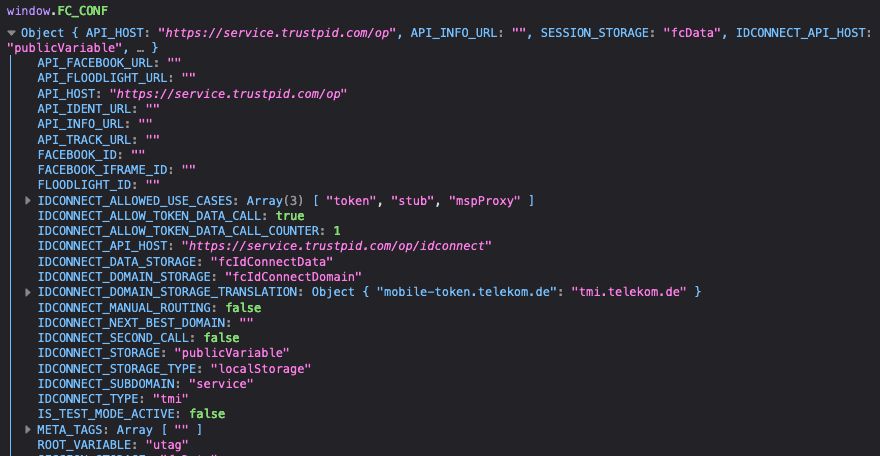
Looking at how the code executes on Trustpid's site when I try to verify my nonexistent ID, it appears to be putting operational data on the window object that includes an API call to get your ID, perhaps the ID is not visible except to the API which delivers it to local storage?
-
Not sure how secure that is, presumably they are depending on the headers on the network request to their API to give them the ID and to return it back. Interestingly it looks like revealing the ID may not be the only thing the ID does...
-
It looks like Trustpid is set up to also sync with some Facebook API and the "Floodlight ID" which is the cross-site process Google has for doing conversion tracking (not the new more private proposed process, the old one - support.google.com/searchads/answer/7298761?hl=en )
-
The implication here is that the process to reveal the ID by requesting it from the Trustpid API may not just give the ID to the site that requests it, but also may synchronize other user data across multiple platforms.
-
-
Anyway, don't forget that T-Mobile is already doing this in the US and is only opt-out. vox.com/recode/22325420/t-mobile-verizon-att-ad-targeting-data 9to5mac.com/2021/03/09/t-mobile-ad-tracking-program-opt-out/ t-mobile.com/privacy-center/education-and-resources/advertising-analytics I can't find anyone who has written about how that works technically, but would be interested in reading.
 Chronotope’s Twitter Archive—№ 148,860
Chronotope’s Twitter Archive—№ 148,860